
Building A CyberLab: Setting up Metasploitable 2 VM
Metasploitable 2 is an intentionally vulnerable virtual machine built by metasploit. It’s goal is to allow hackers or penetration testers practice on existing vulnerabilities without impacting real world systems. To do so in our case, we are going to isolate the metaploitable 2 VM in our internal network protected by pfSense, our virtual firewall. Download the Metasploitable 2 VM following the link bellow:
https://sourceforge.net/projects/metasploitable
- Once downloaded, unzip the file. You should have a new folder similar to the screenshot bellow.

- Now that this is done, open your VirtualBox Machine and click on New button. For the name, enter Metasploitable 2; for type select Linux; and for version select Ubuntu (64-bit). Click Next; make no changes to the page and click Next.
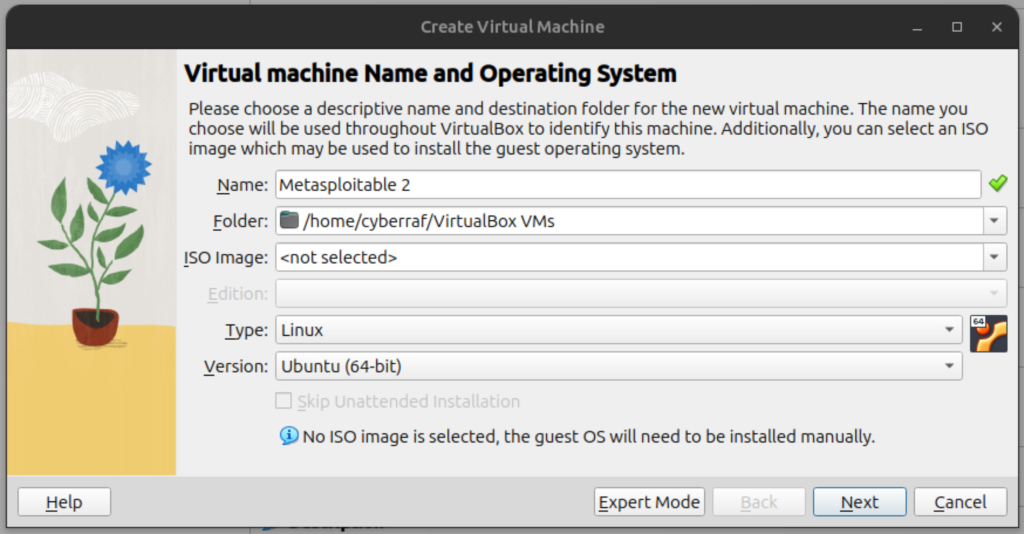
- Select Use and Existing Virtual Hard Disk File; click on the Folder icon and click on the Add button and navigate to the folder in which metasploitable was unzipped in to select your file. Click the Choose button.
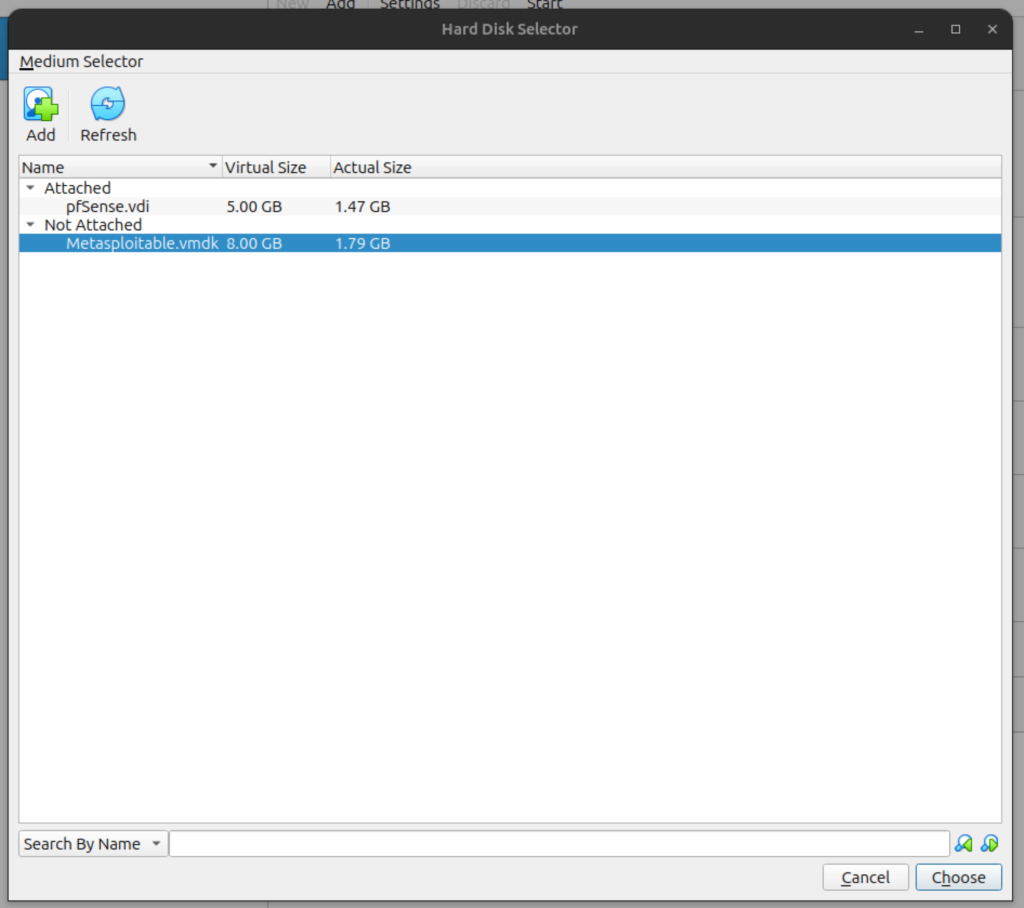
- Click Next then Finish.
- Right click on the metasploitable 2 machine created and click on Setting then Network. Under Adapter 1, check the box Enable Network Adapter and under Attached to, select Internal Network. Select Internal LAN (the internal network we previously created) and press OK.
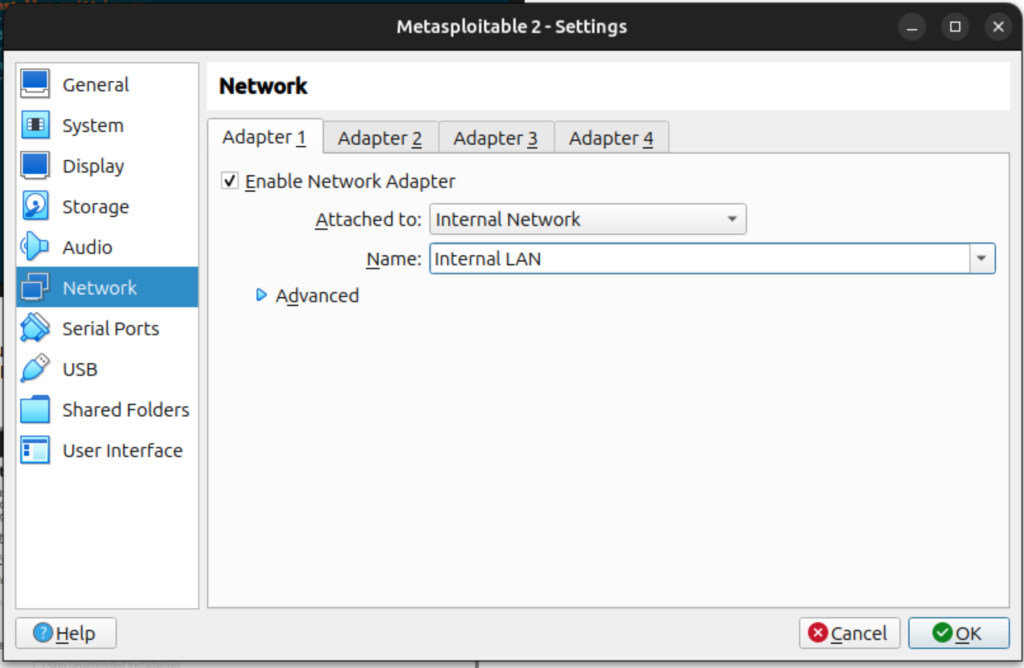
- Double clcik on the Metasploitable 2 machine to open it.
Login is msfadmin and password is msfadmin
